Real-time threat detection and response with AI-driven security analytics. Our NSOC Security Operations Center ensures continuous surveillance of your IT infrastructure to detect and prevent cyberattacks before they escalate. We utilize AI-powered analytics and automated response mechanisms to enhance security efficiency
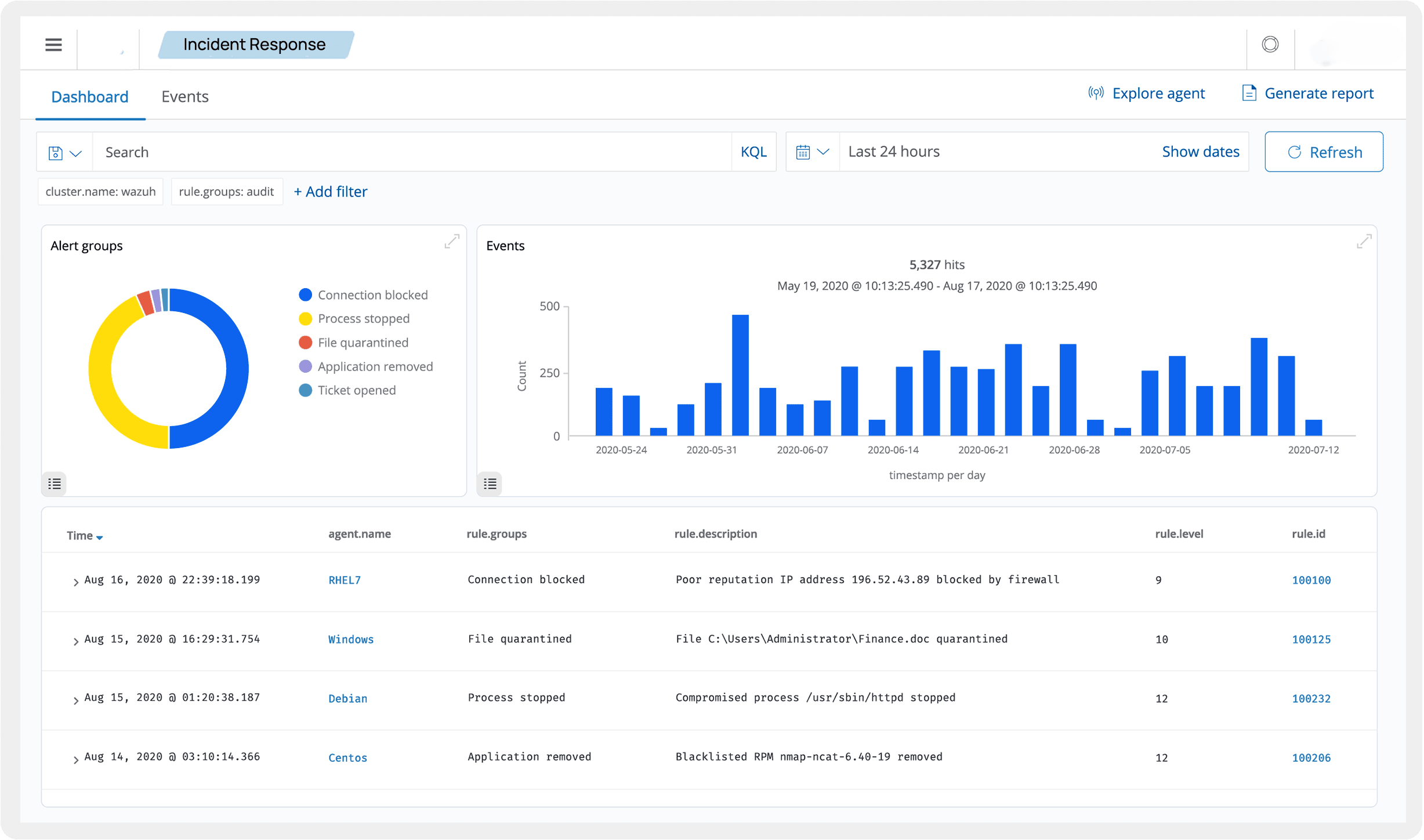
Detect, analyze, and respond to threats with next-gen SIEM & XDR solutions. NSOC integrates Security Information and Event Management (SIEM) with Extended Detection and Response (XDR) capabilities, ensuring real-time insights into your security landscape.
Achieve regulatory compliance and minimize security risks effortlessly. With NSOC, businesses can ensure adherence to critical security standards while mitigating operational risks. We help you stay compliant with industry regulations and reduce cyber liability.
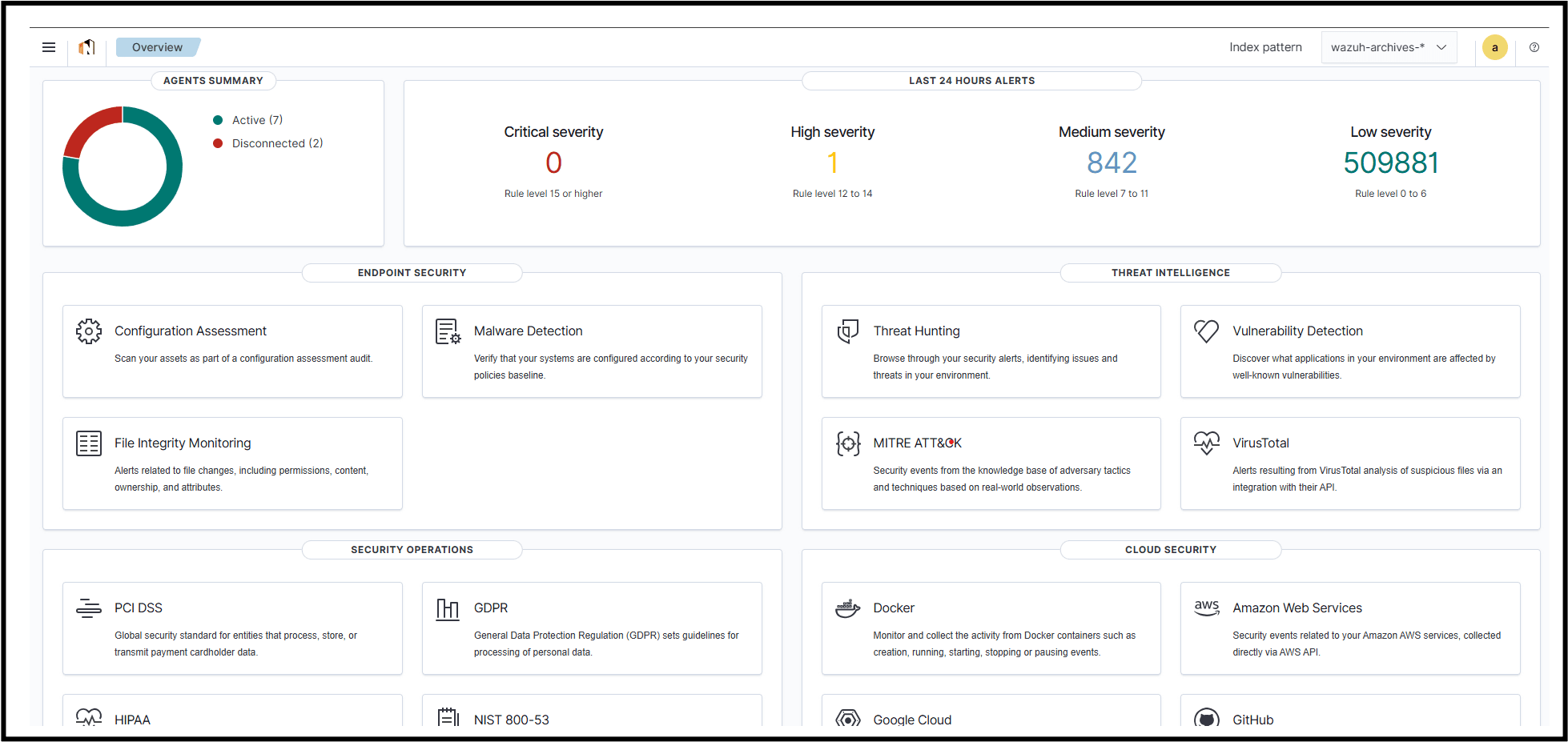
Whether you’re a small company or a large enterprise, our service adapts to your needs, ensuring continuous protection and peace of mind.
Real-Time Threat Detection
Instant detection and response to security threats in real-time, ensuring your systems are always protected.
Compliance Monitoring
Stay compliant with industry standards by continuously monitoring your security posture for various regulations.
Centralized Log Management
Efficient log collection and analysis from all endpoints to identify potential vulnerabilities and incidents.
Automated Incident Response
Automatically trigger actions based on predefined security rules to mitigate threats without delay.
Scalable Architecture
Easily scale your security infrastructure to accommodate the growing needs of your organization or clients.

Leverage real-time intelligence to defend against modern cyber threats. NSOC’s Threat Intelligence Platform continuously collects, analyzes, and mitigates cybersecurity threats, ensuring proactive defense. Our AI-driven incident response mechanism ensures swift mitigation and containment.
Experience the Insights of our Top Rated SOC Services - Read our Clients' Frequently Asked Questions to Gain an Improved Awareness of Our Offerings.
